Unix-liked OS is a kind of stable, multi-user, multi-tasking OS for servers, PCs and even mobile devices.
The UNIX OS is made up of three parts: the kernel, the shell and the programs.
- Kernel is the hub of the OS, which allocates time and memory to programs and handles the files and communications.
- Shell acts as an interface between the user and the kernel. It's a command line interpreter (CLI).
I. Basic Commands
1.1. Listing files and directories
- % ls : When you first login, your current working directory is your home directory. Your home directory has the same name as your user-name, which is where your personal files and subdirectories are saved. To find out what is in the current working directory (except hidden files), type % ls
- To list all files (including those hidden files whose names begin with a dot), type % ls -a
1.2. About Directories
- % mkdir myunixex // To make a subdirectory called myunixex in current working directory.
- % rmdir directory // Remove a directory (if it's empty).
1.3. Changing to a different directory
- % cd [another directory] // To change the current working directory to 'another directory'.
- % cd . // (.) means the current directory. (..) means the parent directory.
- % cd / % cd ~ // cd with no argument or ~ always returns to home directory.
1.4. Path names
- % pwd // Print Working Directory --- to find out the absolute path name of current directory
1.5. About Files
- % cp file1 [file2] // file1 is the source that may contain path name. file2 can be a (.), which means the the target is in the current directory with the same name.
- % mv file1 [file2] // move or rename file1 to file2. file2 can be a directory with a (.)
- % rm file // Remove/delete a file
- % touch file // Create a file
- % cat file // Display a file - concatenate
- % less file // Display a file a page at a time [space bar]= see next page; [q] = quit
- % head file // Display the 1st few lines of a file
- % tail file // Display the last few lines of a file
- % grep -i 'keyword' file // Print each line containing the keywords - case sensitive [or -i ]
- -v display those do NOT match. -n also display line number; -c total count of matched lines
- % wc [-l] file // Count number of [-l] lines/ [-w]words/characters in file.
1.6. Wildcards & File Name conventions
- (*) (?)
- In naming files, we should avoid using special characters such as (/ * & %) and space.
- Use only letters, numbers, _ (underscore) and . (dot)
- File names conventionally start with a lower-case letter, and may end with an extension name.
- Directory is a special type of file, so is subject to the file name conventions.
1.7. Getting Help
- % man command // To read the manual page for a command.
- % whatis command // To give a one-line description of the command.
- % apropos keyword // When you are not sure the exact name; Match commands with keyword.
II. Security
2.1 File System Security (Access Rights)
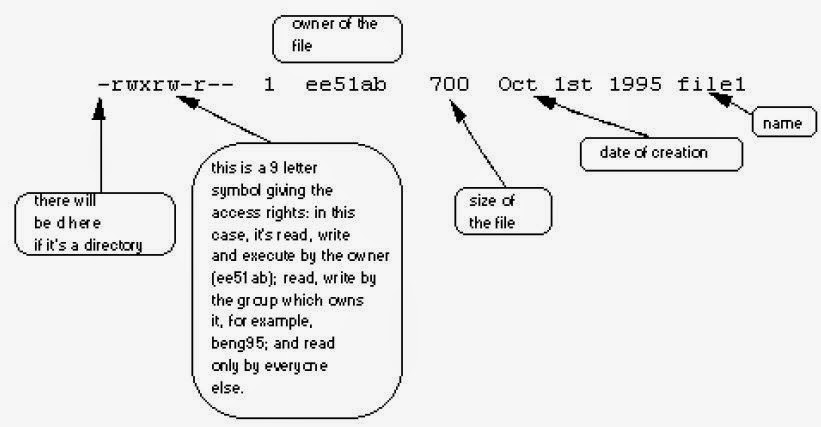
- % ls -l // [-l] for long listing. We'll see details similar to the example below.
- We will find that each file (and directory) has associated access rights
- Access rights on files: r (read/copy) w (write/change) x (execute)
- Access rights on directories: r (list) w (delete/move files) x (access files with given permission)
- To read a file, you must have x permission on the directory containing that file & all parent directories.
- Change Access Rights:
- % chmod go-rwx file1 //remove rwx permissions on file1 for group & others
- % chmod a+rw file1 // Give read & write permissions on file1 to all.
2.2 Processes and Jobs
- A process is an executing program identified by a unique PID (process identifier).
- % ps // To see info about your processes (with associated PID and status).
- A process may be in the foreground / background / suspended.
- Usually, shell doesn't return the Unix prompt until the current process has finished executing.
- A long process can be in background, so the Unix prompt can return immediately, and other tasks can be carried out while the long process continues executing.
- To background a process, type an & at the end of the command line.
- % sleep 10 // wait 10s
- % sleep 10 & // wait 10s in background, return [job #] PID
- % sleep 1000 then [Ctrl ^]+Z to suspend the process, then % bg //put it in background
- Do not background programs that require user interaction (e.g. vi ).
- % jobs // To see the list of processes (running/background/suspended)
- In format as: [job#] Status Process_Name [Process_options]
- % fg [%job#] // To restart (foreground) a suspended processes.
- If no option, then foreground the last suspended process.
- ^ + C // To kill a job running in the foreground.
- % kill %job# // To kill a suspended or background process.
- % kill PID# // To kill a process by PID_number
- If a process refuses to be killed, use -9 option. % kill -9 PID#
- It's not possible to kill off other user's process.
2.3 Role Based Access Control (RBAC)
* Installation / Configuration of RBAC and sudo- Loading the VirtualBox image (.vbox) of a pre-installed Fedora Core 8 machine.
- If start from a fresh Fedora Core 8 iso:
- Install the policy
- Open up a terminal and become root
- Default user: dmao Admin user: root
- dmao@localhost:~$ su - enter password
- root@localhost:~# killall -9 yum-updatesd // close yum-updatesd that prevents us from installing software, it's for providing notification of available updates.
- Install our example devel policy
- Integrate our example policy for a cash registry system
- Load our cash registry policy: :~# semodule -i cash_register.pp
- Creating the users
- Create our cashiers' account with password.
- ~# adduser alice adduser bob passwd alicepd1 passwd bobp2
- Give our users a role and the capacity of login to the system:
- Create our working dirs for our /bin/register.py program
- Put the right contexts for the folders and access to them using fixfiles.
- We may allow some user to have more than 1 role by using gedit.
- Try the policy
- Ctrl-Shift-F2 and login as alice, the cashier (cashier_r)
- Try to cheat the system by committing as a cashier
- Ctrl-Shift-F3 and login as bob, the manager (mgr_r), and confirm what alice counted
- As bob, try to cheat in a different value and commit it.

No comments:
Post a Comment